Table of Contents
- 1 The Importance of Having a WordPress Security Checklist
- 2 Is WordPress Safe or Is WordPress Secure?
- 3 WordPress Security Guide: 13+ WordPress Security Issues You Need to Know for Your Directory Website
- 3.1 1. Unauthorized Logins
- 3.2 2. Outdated Core Software
- 3.3 3. Undefined User Roles
- 3.4 4. Outdated Themes and Plugins
- 3.5 5. Malware
- 3.6 6. Structured Query Language (SQL) Injections
- 3.7 7. Search Engine Optimization (SEO) Spam
- 3.8 8. Cross-Site Scripting
- 3.9 9. Distributed Denial of Service (DDoS) Attacks or Denial-of-Service (DoS) Attacks
- 3.10 10. Phishing
- 3.11 11. Supply Chain Attacks
- 3.12 12. Hotlinking
- 3.13 13. Lack of SSL Certificates or HTTPS
- 4 Bonus: WordPress Security Guide (Advanced)
- 5 Best WordPress Security Plugins
- 6 What to Do If Your WordPress Website Gets Hacked
- 7 Wrapping up
The Ultimate WordPress Security Guide for Directory Websites – Step by Step (2025)
Despite being the most popular CMS or Content Management System on the planet Earth, WordPress has a striking record of getting hacked. Luckily, there are so many ways to thwart the attempts of hackers, yet only a few people use them.
If you have a WordPress directory site, the pursuit of security is paramount. That’s because, you never want to lose time, money, and energy, do you? Once your website gets affected by hackers it can ruin your business’s reputation and can also snatch the authority away.
Thus, it is worth trying to check the threats and vulnerabilities of your website and take the necessary steps to prevent all unexpected disasters. Sadly, there are innumerable threats your website may face over the course of mere a day.
Luckily, most of the threats and attacks are interrelated and so detecting only a handful of them and blocking them will keep your website safe from almost all the disasters.
In today’s article, we will go over 10 WordPress security concerns of a WordPress directory website and the ways to deal with them. So, let’s get started.
The Importance of Having a WordPress Security Checklist
Ensuring security is a mandatory term for all websites whether it is WordPress or custom. But as a popular platform, WordPress websites are mostly attacked by the hackers. Form a simple blog to large enterprises, a proper WordPress security checklist is your first line of defense against these risks. It helps to ensure cover up your all-important security tasks. Maintaining an optimized checklist can extend to protecting sensitive data, safeguarding your reputation and complying with legal requirements. Here’s why every WordPress website, no matter the size, needs a security checklist:
1. Protection from Cyber Threats
WordPress’s popularity makes it a frequent target for hackers. With a proper security checklist, you take protective steps to defend against cyber threats such as brute force attacks, SQL injections, and cross-site scripting. By regularly reviewing and updating your security practices, you can stay one step ahead of potential attackers.
2. Safeguarding Sensitive Data
If your website stores sensitive customer information, such as email addresses, login credentials, or payment details, a security checklist can help to keep this data remains secure by taking protective steps. It helps mitigate the risk of unauthorized access, data breaches, and identity theft, keeping both your business and your customers protected.
3. Compliance with Regulations
Various industry regulations require businesses to adhere to strict security protocols to protect user data. Breaking the laws can cause a huge monetary lose. A well-organized security checklist ensures that your website is compliant with data protection laws, helping you avoid costly fines and legal penalties.
4. Maintaining Customer Trust
A security breach can damage your brand’s reputation entirely. Breaching customer’s confidential data like name, address or phone number can lose trust, leading to a decline in engagement and conversions. By using a security checklist, you minimize the risk of such incidents. It ensures your website remains a secure space for customers to interact with your brand.
5. Improved SEO Performance
A secure site with an SSL certificate and other security measures will not only protect your visitors but also boost your search engine visibility. Conversely, an insecure site flagged for malware or hacked content could be removed from search results or display security warnings, which can drastically hurt your SEO and traffic.
6. Preventing Downtime and Loss of Revenue
Downtime caused by security breaches or malware infections can result in lost sales, frustrated customers, and a damaged reputation. A WordPress security checklist helps ensure that your website is up and running smoothly, maintaining optimal performance, fast loading speeds, and an excellent user experience.
7. Avoiding Legal Consequences
In case of a data breach, your business could face legal repercussions, including lawsuits and fines, especially if sensitive customer data is compromised. A comprehensive security checklist helps mitigate this risk, ensuring that you’re following the best practices for securing your site and data.
Whether you’re a seasoned WordPress user or a beginner, a security checklist provides a reliable resource to help you manage your site’s safety. Even experienced security professionals can benefit from having a checklist on hand, as it serves as a reference to ensure no crucial task is overlooked. By following a checklist, you can avoid the unwanted issues of your WordPress websites.
Is WordPress Safe or Is WordPress Secure?
Definitely! WordPress core developers regularly come with necessary WordPress security updates to keep your website as safe as possible. In fact, it ticks all the boxes to keep your website secure. So, no worries!
However, from your end, you must make sure you are following the best practices to keep your WordPress website secure and safe. If you don’t know the best practices, go through the entire post. Please note that your WordPress website is vulnerable if you are not following these best security practices. Plus, make sure you never turn off any WordPress security services from the backend or by using any plugin.
WordPress Security Guide: 13+ WordPress Security Issues You Need to Know for Your Directory Website
We have not just handpicked these WordPress security problems but also explained ways to avoid them. You can use this article as a WordPress security guide for your website
- BruteForce Attacks via Unauthorized Logins
- Outdated WordPress Core
- Undefined User Roles
- Outdated Themes and Plugins
- Malware
- Structured Query Language (SQL) Injections
- Search Engine Optimization (SEO) Spam
- Cross-Site Scripting
- Distributed Denial of Service (DDoS) Attacks
- Phishing
- Supply Chain Attacks
- Hotlinking
- Lack of SSL or HTTPS
- Bonus: Advanced Tricks
Have you ever heard of “Brute Force” attacks? In case you didn’t know, a Brute-force attack is when a hacker tries to login billions of times by potential combinations of username and password with the assistance of a bot.
If they can somehow match with the exact credentials, you are done. Meaning the hackers will gain all the administrative access to all the protected and private data of your website.
Your WordPress directory site is vulnerable due to the comparatively easy-to-find default login page. Anyone, including a hacker, knows the default login page URL that is “append/wp-admin” or “append/wp-login.php”.
Most of the hackers take this opportunity and gain access to the login page to perform a brute force attack.
WordPress security check: How to avoid a Bruteforce attack on a WordPress Directory website?
- Customize the default URL of the login page so that it is harder to find for hackers. Get rid of the default “admin” and use a secret username to dodge the guess of the hackers.
- Deploy reputable WordPress security plugins that limit the login attempts by adding captchas, necessary to root the brute force attack out. These security tools will also conduct important WordPress security scans.
- Use two-factor authentication so that the hacker needs your other device to carry out the login attempts.
- As a WordPress user, never skimp on setting a complex password. That means use at least 12 character password lengths including uppercase, lowercase, special characters, as well as numbers.
Adding a bit of complexity to your password makes it surprisingly powerful to save your day. If you are not convinced yet, take a look at the following table showing an algorithm of how much time it would take to perform a brute-force attack at a rate of around a billion per second where:
LC = Lower Case Characters,
UC = Upper Case Characters,
SC = Special Characters, and
Digits.
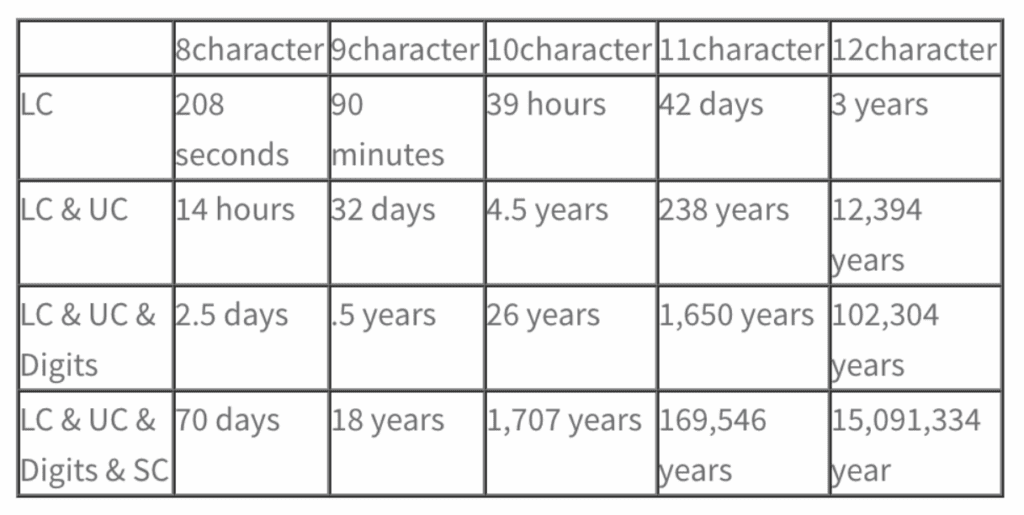
As shown, using a password with a combination of character types and/or length will make it nearly impossible for a brute-force attempt to be successful.
See? Using a combination of all sorts of characters having a good length makes it nearly impossible for a hacker to perform a successful brute force attack.
Remember, a brute-force attack can be performed anywhere a login is required using a username and a password. So, never forget to fortify your credentials to nip the brute-force attack and stay carefree.
2. Outdated Core Software
Gone are the days when people had to create a professional website from scratch hiring web developers. It was not only an expensive but also a time-consuming process. The best part of using WordPress is you can build a professional website without having any coding know-how or hiring professional web developers.
For development and maintenance purposes and to address other security concerns, the WordPress team regularly enhances its features and sends updates over the air. Generally, they roll out updates every other 3 months or so. Unfortunately, although it might be cool, WordPress does not update your website on its own.
Now, as the update is not automatic, the onus falls on the user on whether to update. If you do not update your WordPress core as a CMS, you are pushing your website to vulnerabilities.
If you are not updating your core software, you may not be able to update the other themes and plugins either. Which makes your website more susceptible to hackers.
WordPress security guide: What You Should Do
- Since WordPress does not make your site automatically updated, you have to do it on your own. To update your WordPress core, log in to navigate to the WP Admin Dashboard and click on the ‘Updates’ option. Hit the ‘Updates’ option:
Now, you can click on the “Update Now” button to start the process.
Please note that you should take a backup of the database file before upgrading the core software.
- Another way to do it is, once you login to your WP Dashboard, you will usually see the following message:
From here, you can easily upgrade your WordPress core.
Keep in mind that WordPress core developers always try to provide you a safe, seamless, and snappy experience via software updates.
3. Undefined User Roles
In a WordPress site, you will get 6 different user roles. They are:
- Subscriber
- Contributor
- Author
- Editor
- Admin
- Super Admin
Now, if you do not assign these user roles to the right individuals, hackers might gain access to your backend too easily. For example, a user with an editor role has not only the power to write and publish content but also has the control to delete any content.
Then again, a user with an Administrator role can have all the permissions to take any action throughout your website such as changing the password of other admins, modifying the themes, plugins, and even core software.
WordPress security guide: What You Should Do
When you are giving too many permissions to certain users by assigning admin, editor, author, and contributor user roles make sure they are trustworthy and won’t mar your website.
“To err is human”. So, check and double-check your website’s users who are particularly enjoying the admin, editor, author, and contributor user roles. Remember, the wrong person with these user roles might give their credentials to the hackers to steal priceless data.
4. Outdated Themes and Plugins
As WordPress is customizable with hundreds of themes and plugins, chances are very high that you will use a bunch of plugins or themes on your website.
However, like core WordPress updates, the authors of themes and plugins also release updates with security patches. Now, like WordPress core, you must update these plugins and themes too.
If you only update the WordPress core and skip updating the themes and plugins, hackers might use them as entry points to gain access to your site.
WordPress security audit: What You Should Do
Simply go to the WP Admin Dashboard > Plugins then manually update the plugins. Or, you can also use an automatic plugin updater to do so to avoid vulnerabilities or WordPress security issues.
5. Malware
Malware is when a hacker places malware files or implants code in your website’s existing files to steal sensitive data from your website.
As we already mentioned, if you do not update your WordPress core and its themes and plugins, hackers might take this opportunity to attempt an unauthorized login via “backdoor files” and thus eventually wreak havoc on your website.
What You Should Do
- Carefully vet your plugin or themes on WordPress.org before you install them.
- In the world of WordPress, everything can be done just by using plugins. So, simply, use a reputed WordPress security plugin to check if any Malware exists on your site and repair damaged files.
6. Structured Query Language (SQL) Injections
Attackers use this language to inject malicious codes and quickly gain access to the stored data of your website. During such an attack, hackers gain the opportunity to directly view and edit your site’s database.
With SQL injections, hackers can add unauthorized links and contents, make new accounts, leak, edit and delete data.
Most of the time, hackers use the visitors’ endpoint to insert malicious codes. For example, attackers take the opportunity to insert malicious codes using front-end submissions like contact forms or things like this.
What You Should Do
- Restrict inserting any kind of data using special characters to make a string of malicious codes into harmless gibberish. If you are a non-techy user, deploy WordPress security plugins to make it work for you.
- Consider using reCaptcha images to stop bots from inserting malicious codes on the contact forms or any other input fields.
7. Search Engine Optimization (SEO) Spam
Search Engine Optimization Spam is similar to SQL injections but in this case, the hackers target your top-ranking pages. The hackers fill out your pages with spammy keywords, popup ads to sell their items or counterfeit merchandise.
For instance, they will inject keywords like “best mobile phone under 10k dollars”. So, if people search for keywords like “best mobile phone under 10k dollars”, your already ranked page will appear on the SERPs which you will never want.
These attacks are much harder to detect as after getting access to the pages the hackers wait to insert those spammy keywords or ads so as not to make their activities discernible.
Hackers can perform these attacks for the same reason SQL injection happens, that is when you use outdated WordPress core, outdated themes, or plugins.
WordPress security guide: What You Should Do
- Use a quality WordPress security plugin to detect or protect from SEO spam.
- Watch your top-ranked web pages to determine if they are ranking for any spammy keywords, not related to your website.
- Go over to your website’s analytics data to see a sudden change in any webpage’s SERP positions or even in any event like a sudden influx of traffic without any apparent reason.
Regardless of the routes you choose, you must take action early on so that you can avoid any search engine crawler’s strike to your high-performing page to save the hard work you put in.
8. Cross-Site Scripting
Similar to SQL injections, Cross-site Scripting or XSS attacks occur when a hacker tries to implant and run malicious code to the backend files of your website to target your website’s functionalities.
During a Cross-site Scripting attack, the hacker gains access to the backend and shows fake input fields on the frontend like fake contact forms to steal user data or shows disguised links to a low DA(Domain Authority) website or any other faulty websites.
Again, outdated WordPress core, outdated themes, and plugins are the reason Cross-site Scripting attacks happen.
WordPress security guide: What You Should Do
- Update your plugins, themes, and WordPress core in time so that the hackers can’t make their way to the backend.
- Use WAF (web application firewall) plugins to prevent the hackers from exploiting your plugins to access files dictating to your website’s frontend and protect your WordPress site from XSS, SQL injections, and other attacks.
- Be careful when implementing any third-party plugins.
9. Distributed Denial of Service (DDoS) Attacks or Denial-of-Service (DoS) Attacks
When a Denial of Service or DoS happens, your site may become down and you may find it hard to rebuild your reputation. During such an attack, the hackers usually send too much traffic to the server at a time by using multiple machines. Consequently, the server crashes taking down all its hosted websites. It’s a much worse attack than you might think.
That’s because the site administrator along with all the visitors gets blocked from accessing the website.
WordPress security guide: What You Should Do
- Find a reliable WordPress hosting service provider who prevents any DoS attack on your website.
10. Phishing
Phishing is a term that came from actual fishing. In an attempt to phish someone, the hackers write compelling texts with spammy links showing credible email addresses or phone numbers or so. If someone clicks on such malicious links, they might lose all their personal data.
Unfortunately, WordPress does not prevent you and your visitors from such malicious click baits. Once, your users lose their valuable personal information on your website by hitting these spammy links, you will eventually lose their trust.
For your information, we have come up with the following spammy comment which persuades a reader to click:
WordPress security guide: What You Should Do
- Conduct regular updates, monitor site activity, and use secure passwords
- Use reCAPTCHA images to differentiate bot and human submissions.
11. Supply Chain Attacks
WordPress websites are vulnerable to Supply Chain Attacks because they are based on something you can not go away with. These attacks capitalize on the most important features of WordPress – themes and plugins!
Usually, there are two ways this attack can happen. One is when a plugin or theme owner himself or herself injects malware or spammy codes and the other is when a hacker purchases a plugin or theme and injects malware.
In either of the cases, they can get access to the secure files and wreak havoc such as SEO stealing valuable data, spamming, phishing, collecting customer data showing counterfeit forms to the users, and so forth.
Again, these attacks might happen due to the usage of outdated versions of themes and plugins. Thankfully, these types of attacks have a short span of life because they are supervised by the WordPress core developers’ relentless work.
WordPress security guide: What You Should Do
- Install WordPress security plugins that regularly check updates on your website.
- Consider taking a backup of the data of your website.
12. Hotlinking
Hotlinking is when other websites’ owners directly use your hosted image or video links to their site instead of downloading and uploading these. As a result, you will have to pay higher monthly bills to your hosting provider.
Technically, a Hotlinker is not a hacker but he or she is actually using your hosting storage and your copyrighted contents on their website without even giving credit. It’s illegal.
Thankfully, search engines generally take action against such illegal and poor practices.
WordPress security guide: What You Should Do
- Use discernible watermarks on your content like on images or videos.
- Use tried-and-true WordPress photography plugins to easily add watermarks to your content.
13. Lack of SSL Certificates or HTTPS
Be it a WordPress site or any other website, if you have not secured your website with SSL or HTTPS, your site is in danger. For your information, SSL or Secure Sockets Layer is a protocol that encrypts data transferred between the user and your website. This encryption process makes it harder for hackers to sniff around confidential data and steal them.
Many of you may only use HTTP in lieu of HTTPS. But the latter is much safer than the former. Once you enable HTTPS, you will be able to see a padlock sign next to your website address on your browser.
WordPress security guide: What You Should Do
- Get a free SSL from your Domain or Hosting provider. However, if you do not get a free SSL consider buying a paid SSL for your website for the safety of your data and your site’s reputation.
Bonus: WordPress Security Guide (Advanced)
If you do have technical know-how you can try out these tips otherwise we highly recommend you leave it for the professionals:
Disable File Editing
The dynamism of WordPress may also make your WordPress vulnerable. Don’t get me wrong. The built-in code editor for themes and plugins on the admin backend is unquestionably a good feature but it poses a significant WordPress safety threat. So, we suggest you turn this feature off.
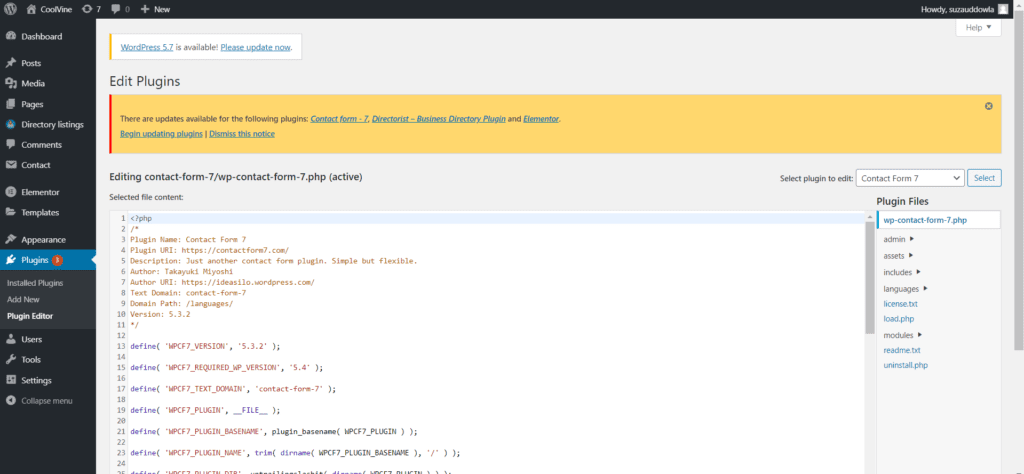
Go to the wp-config.php file and copy and paste the following code:
| // Disallow file editdefine( ‘DISALLOW_FILE_EDIT’, true ); |
Don’t forget to save the changes.
Alternatively, with the free Succuri plugin, you can do this with just a single click using the Hardening feature.
Disable PHP File Execution in Certain WordPress Directories
You can strengthen your WordPress security by simply disabling the PHP file execution in certain WordPress directories where you do not need them. For instance, you don’t need PHP file execution in /wp-content/uploads/.
To stop this feature, open a text editor like notepad ++ and copy and paste the following code snippet:
| <Files *.php>deny from all</Files> |
Next up, save this file as .htaccess and upload it to /wp-content/uploads/ folders on your website using the FTP client.
Alternatively, again, as mentioned above, you can use the Hardening feature in the free Succuri plugin with just a single click to do so.
Change WordPress Database Prefix
WordPress uses the “wp_” as the default prefix for the database. Thus hackers can easily guess what your table name is and so your site becomes vulnerable. However, if do have good coding know-how, you can proceed otherwise, your site can break.
Disable Directory Indexing & Browsing
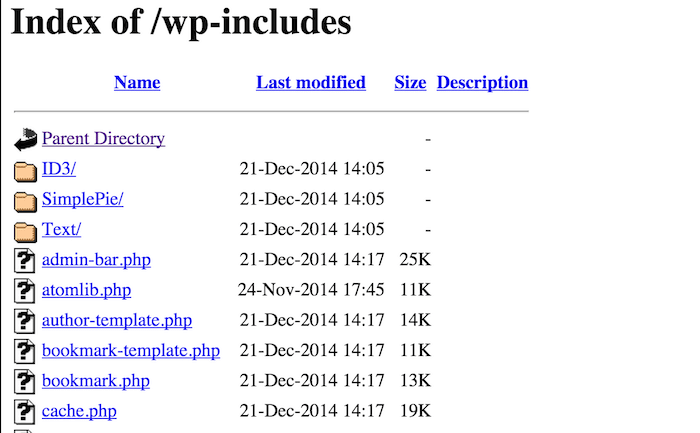
Directory browsing can make your WordPress site vulnerable because a hacker can easily find out your directory structure, sniff around your files and look into sensitive data. So, we highly recommend you to turn it off.
You can turn it off by simply connecting your website using File Transfer Protocol or FTP or cPanel’s file manager. Then from your site’s root directory, locate the .htaccess file and then add the following line at the end of the .htaccess file:
Options -Indexes
Finally, save and upload the .htaccess file back to your site to take an effect.
Disable XML-RPC in WordPress
From the WordPress 3.5 release XML-RPC feature was enabled by default. It helps your WordPress website to connect with mobile apps and the web. Unfortunately, hackers grab this opportunity to perform BruteForce attacks, though it is a powerful and effective feature.
Usually, if you use a login lockdown plugin, a hacker can only try out a few login attempts. After that, all the suspicious login attempts get caught by the plugin.
However, with the XML-RPC feature enabled, the same hacker can call the system.multicall function to try out thousands of login attempts which is flat-out dangerous for your WordPress website’s security and safety.
Luckily, the web application firewall we mentioned earlier can take care of this issue.
Automatically log out Idle Users in WordPress
Like many other banking and financial applications, you can implement this feature on your WordPress website to increase its safety. Because, a user can wander away from his or her session, which amplifies the risk of getting hijacked.
This poses the risk of changing passwords or making other changes to their account. So, we recommend you implement this feature. You can do this by simply using a WordPress inactive logout plugin.
Add Security Questions to WordPress Login Screen
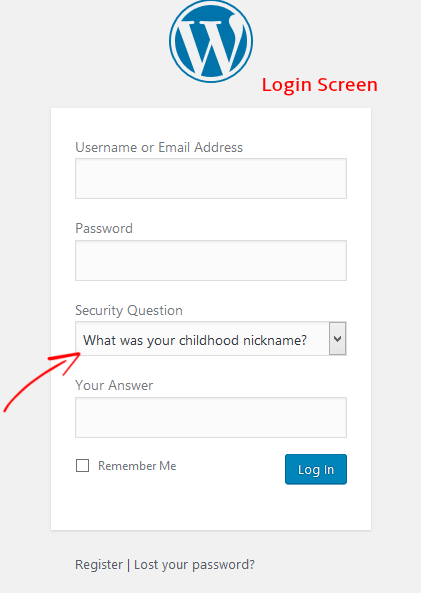
If you add a security question to log in to your WordPress website, it makes it even harder for hackers to perform unauthorized login. You can effortlessly add security questions using a WordPress security question plugin.
Best WordPress Security Plugins
Choosing a good WordPress security plugin can help to protect your WordPress directory website from unwanted threats.
Whether you’re running a simple directory or a multi-directory with lots of listings, the right security solution can defend against cyberattacks, safeguard sensitive data, and enhance your site’s performance.
Below, we’ll review some of the best WordPress security tools that can help keep your website safe and secure.
1. Cloudflare
Cloudflare is a top-tier WordPress security solution. Cloudflare offers a lot of features, including a powerful firewall, DDoS attack protection, and a browser integrity check. Besides, it’s CDN (Content Delivery Network) caches static content across global servers that enhance page load speeds. Additionally, the WordPress plugin allows users to manage DNS records, view site uptime, and handle SSL certificates directly from the WordPress dashboard. After switching to Cloudflare, many users have seen noticeable improvements in security and overall website stability.
2. Sucuri
Sucuri is an effective WordPress security solution that offers solid protection against cyber threats. With its advanced firewall, Sucuri blocks brute force and malicious attacks before they reach your server. Including core features, it has multiple features like blacklist monitoring and protection against SQL injection and cross-site scripting attacks. The solution is also bundled with CDN, ensuring faster loading times for websites. Sucuri’s free plugin is a great option for basic security, but its premium plans offer more extensive protection and advanced features.
3. Wordfence
Wordfence Security is another popular and powerful WordPress security plugin that combines simplicity with strong protection tools. It offers strong firewall features with country blocking, brute force protection, and real-time threat defense. The free version provides essential features such as malware scanning and login security. But for advanced features like real-time traffic monitoring and incident recovery tools, a premium tier is required. Wordfence is particularly useful for developers, offering discounted pricing for multiple licenses.
4. MalCare Security
MalCare Security provides cloud-based malware scanning with intelligent detection algorithms. It can identify and remove threats across your entire site. It includes a one-click malware removal tool and a firewall that blocks bots and other malicious intrusions. MalCare also offers uptime monitoring and immediate notifications in case of attacks. The plugin is lightweight and doesn’t slow down your website, making it a fast and effective solution for site security.
5. All In One WP Security & Firewall
All In One WP Security & Firewall is another WordPress security plugin that is getting popular for its easy interface. It has an easy interface with visual graphs to track your website’s security status and specific problem areas. This plugin focuses on account protection, login security, user registration, and database security. It also includes a temporary lockdown feature for emergency situations, as well as the ability to export and import specific security settings.
What to Do If Your WordPress Website Gets Hacked
No one wishes to lose their website. But sometimes, the bad thing happens. Finding out that your WordPress website has been hacked is painful, but acting quickly can help to minimize the damage and recover the site. Follow these steps to recover your site and restore its security:
1. Separate the Website
If you have single or multiple sites on the same server, separate the hacked site immediately to prevent the attack from spreading. This may have to take the site offline for a short time to prevent any more damage.
2. Restore from Backup
For restoring the website, use latest backup file. If you haven’t backed up your site recently, next time, don’t forget to keep a backup.
3. Change All Passwords
Make sure to update the all user accounts passwords. Make sure to use strong, unique passwords for each account to prevent future breaches.
4. Scan for Malware
Use a trusted security plugin to check for any malicious code or any issue. If you have a security plugin already installed, contact the developers for help with cleaning your site.
5. Identify and Remove Suspicious Files
Review your site’s files and folders for any unusual or suspicious files. Malicious code is often injected by hackers into core files, themes, or plugins.
6. Clean the Database
Make sure to review your WordPress database for any changes that weren’t authorized. Restore any altered tables or entries back to their original state to ensure no malicious content remains.
7. Review User Accounts
Double check your list of registered users. Remove any suspicious or unauthorized accounts. Make sure there are no unknown administrators with access to your site.
8. Notify Affected Users
If the hack exposed sensitive user data, you must comply with data breach notification laws. Notify affected users and provide them with the necessary information to protect themselves.
By following these steps, you can quickly regain control of your WordPress site and prevent further damage.
Wrapping up
That’s all! We hope this article will help you keep your WordPresss directory website secure and safe. However, we will be updating this post over time with newer tips and tricks. So, stay connected for future updates.

If you liked our posts, don’t forget to subscribe to our blog so that we can notify you once any post is published. Directorist is now on Facebook, Twitter, and LinkedIn! You can also join the Directorist Community for sharing your thoughts and experiences relating to the directory niche. Come and join us to see what we’re up to.
2 Comments
Leave a Reply
You must be logged in to post a comment.




andrew
August 24, 2022This was a very informative blog and I really enjoyed reading it. But I also have a few points regarding it to discuss with you.
WordPress is the most popular Content Management System (CMS) for websites. The free version makes it easier to get started. Businesses rely on WordPress every day to create their sites.
Here are some factors that you must consider in order to secure your WordPress website:-
1. Protect against SQL injections
2. Get a web application firewall
3. Hardening Database Security
Md. Hamim Khan
September 6, 2022Thanks for your points